Cyfinoid Research - Attack and Defend Software Supply Chain - DCTLV2025
Name of Training: Attack and Defend Software Supply Chain
Trainer(s): Anant Shrivastava
Dates: August 11-12, 2025
Time: 8:00 am to 5:00 pm PT
Venue: Las Vegas Convention Center
Cost: $1800
Course Description:
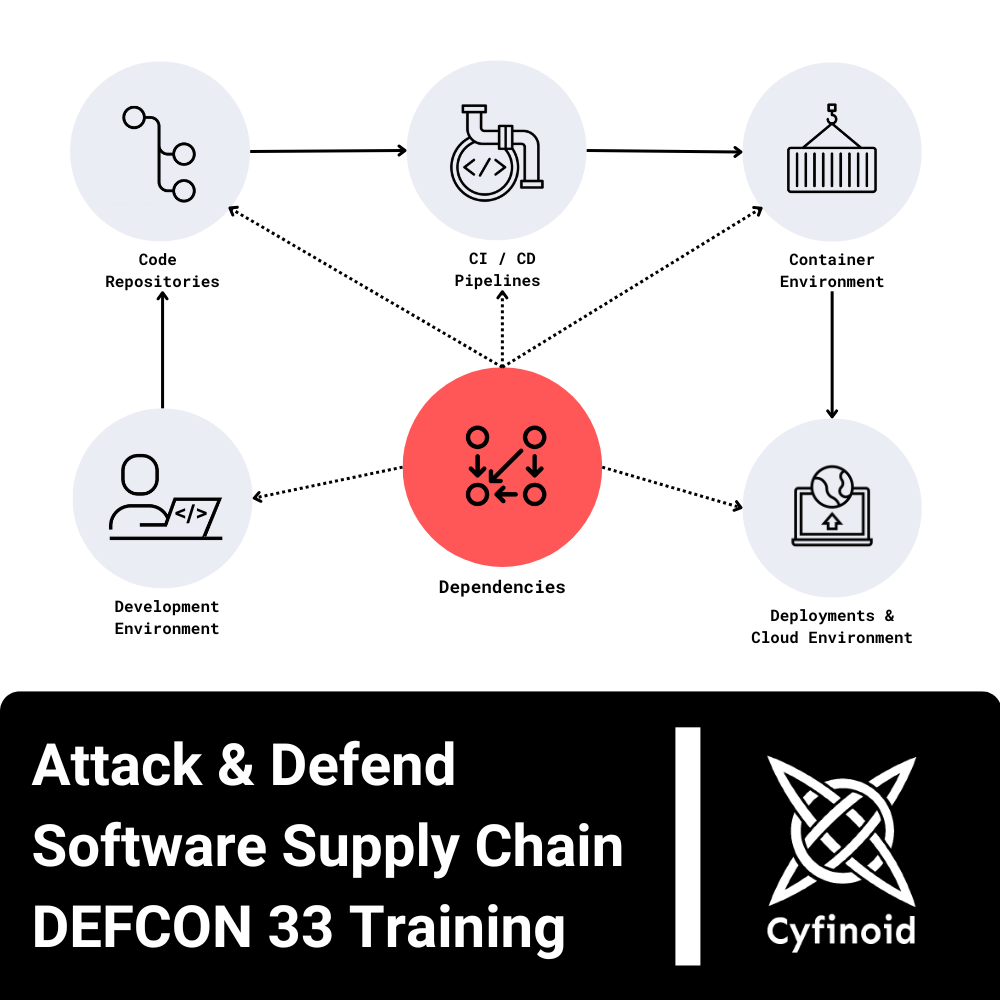
In today's interconnected world, software development relies heavily on third-party components---up to 80% of your code could come from external sources. This reliance creates a complex web of dependencies, making your software supply chain a prime target for cybercriminals. Securing it is no longer optional; it's essential.
This hands-on course takes a comprehensive approach to attacking and securing the software supply chain. In the first section, you'll assume the role of a sophisticated attacker, infiltrating an enterprise through its supply chain partners. You'll learn how to compromise developer laptops, code repositories, CI/CD pipelines, internal registries, and even production environments. Once you've seen how vulnerabilities can be exploited, we'll pivot to defense.
In the second section, we'll build and secure a GitHub organization, configure repositories, and implement best practices to mitigate risks. You'll learn how to secure IaC (Infrastructure as Code) assets, validate third-party code, and remediate vulnerabilities to ensure end-to-end protection.
Through practical exercises, you'll apply these strategies to safeguard your developer environments, CI/CD pipelines, and production systems. By the end of the course, you'll have the knowledge and tools to turn your software supply chain into a security strength rather than a liability.
Course Outline:
Section 1: Attacking the Software Supply Chain
Section 1 provides participants with a thorough understanding of the software supply chain's vulnerabilities and the tactics attackers use to exploit them. Through interactive labs and real-world case studies, you'll actively simulate attacks to uncover weaknesses in developer environments, repositories, CI/CD systems, and cloud deployments.
Topics & Labs:
- Introduction to Software Supply Chains
- Beyond Code Dependencies
- Attacking Developer Environments
- Attacking Code Repositories
- Attacking Dependencies and Package Management
- Attacking Containers
- Attacking CI/CD Pipelines
- Attacking Deployment Environments
Section 2: Defending the Software Supply Chain
In Section 2, participants will shift their focus from attacking to defending, learning practical strategies for building resilience into their software supply chains. Using real-world tools and frameworks, you'll explore ways to secure developer environments, repositories, CI/CD systems, and deployment pipelines.
Topics & Labs:
- Introduction to Defense Strategies
- Security Strategy and Governance
- Effective Inventory Management
- Protecting Assets & Baseline Security
- Mapping Roles and Responsibilities
Difficulty Level:
Beginner
Suggested Prerequisites:
Basic knowledge of software development and IT security concepts is assumed. Familiarity with cloud platforms and CICD processes would be beneficial but not mandatory.
What Students Should Bring:
Laptop or Tablet computing devices with browsers that can connect to the internet with Wifi
-
Please ensure that you use devices that are not bound with an extremely strict Web Proxy/DLP
-
Github Account. Not a work-related account
-
Gitlab Account. Not a work-related Account
Trainer(s) Bio:
Anant Shrivastava is a highly experienced information security professional with over 15 years of corporate experience. He is a frequent speaker and trainer at international conferences, and is the founder of Cyfinoid Research, a cyber security research firm. He leads open source projects such as Tamer Platform and CodeVigilant, and is actively involved in information security communities such as null, OWASP and various BSides Chapters and DefCon groups.
Registration Terms and Conditions:
Trainings are refundable before July 8, 2025, minus a non-refundable processing fee of $250.
Trainings are non-refundable after July 8, 2025.
Training tickets may be transferred. Please email us at training@defcon.org for specifics.
If a training does not reach the minimum registration requirement, it may be cancelled. In the event the training you choose is cancelled, you will be provided the option of receiving a full refund or transferring to another training (subject to availability).
Failure to attend the training without prior written notification, will be considered a no-show. No refund will be given.
By purchasing this ticket you agree to abide by the DEF CON Training Code of Conduct and the registration terms and conditions listed above.
Several breaks will be included throughout the day. Please note that food is not included.
All courses come with a certificate of completion, contingent upon attendance at all course sessions.
